Audit: EBAM
Lead Institution: University of Illinois at Urbana-Champaign
Project Leader: Carl Gunter
Research Progress
-
Abstract
This project concerns a methodology for access management called Experience-Based Access Management (EBAM). The methodology is principally applied to hospital audit logs and access controls, although it has broader applicability to access management in other sectors and types of enterprise. - Focus of the research/Market need for this project
When a health provider treats a patient there are high risks associated with missing information about the patient. Hence providers are given broad access to patient data in the Electronic Medical Record (EMR) system. This leads to an insider threat as potentially tens of thousands of provider employees are allowed to access hundreds of thousands of patient records. Current state-of-the art aims to use auditing of access logs to address this threat, but the logs are very large and require automated support. Current techniques provide automated heuristics and basic statistical tests to address this need. This research, and most of the other projects in the SHARPS Audit Cluster, develops and validates better ways to analyze audit logs automatically. The EBAM methodology envisions this as a continuous process improvement strategy in which audit and access control management operate in cycles of review. This strategy allows hospital audit systems a systematic strategy for limiting security threats with minimal impact on workflows and minimal risks to patient safety due to access controls.
- Project Aims/Goals
EBAM can be described in terms of the following diagram
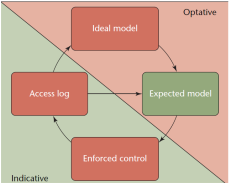
An Ideal Model (IM) describes the rules that would ideally be applied when accessing resources such as patient records in an EMR. The security principle of least privilege says that the system should do its best to enforce the rules in the IM by prohibiting all accesses it views as disallowed. In practice, however, it is often difficult to implement such rules perfectly in the system, so the Enforced Controls (EC) are a working approximation of the IM rules. As the system is used the Audit Log (AL) records accesses that are permitted and rejected by the EC. These can be supplied compared to the IM to determine when an access has been granted or denied when it should not have been. The IM and AL then inform an engineering system known as the Expected Model (EM) of the gaps between the IM and EC as detected by the AL. The EM is used to develop new rules or support actions such as investigations of potential wrong-doing.
- Key Conclusions/Significant Findings/Milestones Reached
Our research on EBAM fell into three general areas of effort: data, anomaly detection, and roles. These were represented in the SHARPS Audit Cluster components DATA, PATHWAYS, and SIMILAR. Our overall conclusion was that there are practical techniques for developing EBAM as a strategy to mitigate risks in hospital access management and that EBAM can benefit from detailed domain-specific knowledge of information about chart users and patients.
Work on DATA involved data and tools for validation. These efforts focused mainly on the curation of a series of access audit log data sets from Northwestern Memorial Hospital (NMH). We also carried out studies with Johns Hopkins Hospitals and Vanderbilt University Medical Center (VUMC). In the last year of this project we began to investigate issues with releasing these types of data sets for study by other researchers. This led us to studies on de-identification for heterogeneous networks (where we focused on social networks) and on de-identification for workflows, represented as sequence data. At a high level our primary conclusion was that security analysis of audit data benefits greatly from detailed domain information about the underlying motives and workflows. For instance, when information about patients in the form of diagnoses is available then this can be used to better understand why particular types of personnel are accessing the records they do. Another high-level carry away is that new techniques are needed to release de-identified heterogeneous network data and sequence data. More details about each of these lines are described in the DATA component report.
Work on PATHWAYS focused on understanding how the sequence of roles of chart users can be used to develop patterns of expected access. We developed a technique for doing this called Patient Flow Anomaly Detection (PFAD), which is described in the PATHWAYS component section. At a high level, we concluded that patient flow data provides a useful and efficient strategy for anomaly detection in hospital audit logs.
The bulk of our efforts on EBAM were part of the component SIMILAR, which primarily investigated techniques to tell when chart users or patients should be viewed as similar to one another. This covered aspects of this problem such as role engineering, characterizing medical specialties, and exploring whether to impose access controls at access time or as part of audit.
- Available Materials for Other Investigators/Interested parties
We published extensively on EBAM and related techniques. A full list of citations follows with more specific lists given for the EBAM component projects (DATA, PATHWAYS, and SIMILAR).
- Market entry strategies
There is a growing market of analytic tools aimed at helping hospitals mitigate risk due to insider threats, where there is a risk of large fines and adverse publicity. The goal of EBAM is to develop techniques to enhance these efforts and better integrate them with other access management systems like role assignments.
Bibliography
Learning a Medical Specialty from a Provider Treatment History
Xun Lu, Aston Zhang, Carl A. Gunter, Daniel Fabbri, David Liebovitz, and Bradley Malin
Under Review
Learning to Discover New Medical Specialties via Patient Treatment Histories
Xun Lu, Aston Zhang, Carl A. Gunter, Daniel Fabbri, David Liebovitz, and Bradley Malin
Under Review
Generative Grammars for Privacy-Preserving Data Publishing
Ravinder Shankesi, Vincent Binschaedler, Aston Zhang, Carl A. Gunter, David Liebovitz, and Brad Malin
Under Review
Decide Now or Decide Later? Quantifying the Tradeoff between Prospective and Retrospective Access Decisions
Wen Zhang, You Chen, Ted Cybulski, Carl A. Gunter, Daniel Fabbri, Patrick Lawlor, David Liebovitz and Brad Malin
Under Review
Diagnosis Based Specialist Identification in the Hospital
Xun Lu
Master of Science Thesis, University of Illinois at Urbana-Champaign, May 2014
Modeling and Detecting Anomalous Topic Access in EMR Audit Logs
Siddharth Gupta
Master of Science Thesis, University of Illinois at Urbana-Champaign, May 2013
Facilitating Patient and Administrator Analyses of Electronic Health Record Accesses
Eric Duffy
Master of Science Thesis, University of Illinois at Urbana-Champaign, August 2013
Privacy Risk in Anonymized Heterogeneous Information Networks
Aston Zhang, Xing Xie, Kevin Chen-Chuan Chang, Carl A. Gunter, Jiawei Han, and XiaoFeng Wang
International Conference on Extending Database Technology (EDBT′14), March 2014
Mining Deviations from Patient Care Pathways via Electronic Medical Record System Audits
He Zhang, Sanjay Mehrotra, David Liebovitz, Carl A. Gunter, and Bradley Malin
ACM Transactions on Management Information Systems (TMIS), volume 4, number 4, article 17, December 2013
Building a Smarter Health and Wellness Future: Privacy and Security Challenges
Carl A. Gunter
Chapter 9 in ICTs and the Health Sector: Towards Smarter Health and Wellness Models, OECD, pp 141-157, October 2013
Requirements and Design for an Extensible Toolkit for Analyzing EMR Audit Logs
Eric Duffy, Steve Nyemba, Carl A. Gunter, David Liebovitz, and Bradley Malin
USENIX Workshop on Health Information Technologies, August 2013
Modeling and Detecting Anomalous Topic Access
Siddharth Gupta, Casey Hanson, Carl A. Gunter, Mario Frank, David Liebovitz, and Bradley Malin
IEEE Intelligence and Security Informatics (ISI 13), June 2013
Evolving Role Definitions through Permission Invocation Patterns
Wen Zhang, You Chen, Carl A. Gunter, David Liebovitz, and Bradley Malin
ACM Symposium on Access Control Models and Technologies, June 2013
Report of Preliminary Findings and Recommendations
State of Illinois Health Information Exchange Authority Data Security and Privacy Committee, September 2012
Tragedy of Anticommons in Digital Right Management of Medical Records
Quanyan Zhu, Carl Gunter, and Tamar Basar
USENIX Workshop on Health Security and Privacy (HealthSec12), August 2012
Role Prediction using Electronic Medical Record System Audits
Wen Zhang, Carl A. Gunter, David Liebovitz, Jian Tian and Bradley Malin
AMIA 2011 Annual Symposium, Washington, DC, October 2011
Experience-Based Access Management: A Life-Cycle Framework for Identity and Access Management Systems
Carl A. Gunter, David M. Liebovitz, and Bradley Malin
IEEE Security & Privacy, September/October 2011
PCAST Workgroup Letter to the National Coordinator
Paul Egerman (Chair), Bill Stead (Vice Chair) and the PCAST Workgroup Members, Office of the National Coordinator for Health and Human Services Health Information Policy Committee, April 2011
