Audit: HIE AUDIT
Lead Institution: University of Illinois at Urbana-Champaign
Project Leader: Carl Gunter
Research Progress
- Abstract
This project concerns technologies for protecting privacy while enforcing security policies on broker based Health Information Exchanges (HIEs). We were inspired by problems emerging from the Illinois Health Information Exchange, especially the problem of providing audit to a system that is expected to keep limited information about patient records. We sought to integrate privacy protection technology and audit review technology. The component has close links to two other components: ENFORCING DISCLOSURE POLICIES and ILHIE PROTOTYPE.
- Focus of the research/Market need for this project
Emerging HIEs including regional, state, and federal exchanges need to deal with concerns about the exchange itself holding too much data. For instance, in state exchanges, citizens often express concern about the government having their health records. Hence these systems are commonly architected as broker systems that transmit data without storing it. This strategy must be integrated with the need to keep audit logs of such transmissions, calling for a balance between what is recorded and what may be needed for an investigation. The HIE AUDIT component focused primarily on developing an appropriate architecture to accommodate both advanced encryption and formal audit functions.
- Project Aims/Goals
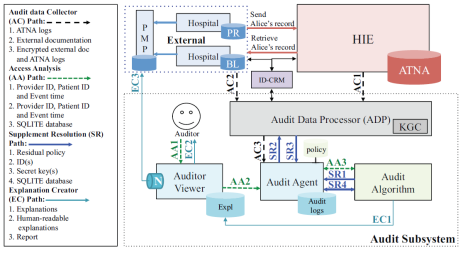
The project considered these requirements and presented a design for auditing broker-based HIEs in a way that controls the information available in audit logs and regulates their release for investigations. Our approach is based on formal rules for audit and the use of Hierarchical Identity-Based Encryption (HIBE) to support staged release of data needed in audits and a balance between automated and manual reviews. We test our methodology via an extension of a standard for auditing HIEs called the Audit Trail and Node Authentication Profile (ATNA) protocol. The following is an architectural diagram of the system.
- Key Conclusions/Significant Findings/Milestones Reached
We developed a system in which Hierarchical Identity Based Encryption (HIBE) is used in coordination with a logic based audit algorithm to limit the amount of information the auditor needs to know to carry out access audit. The system uses HIBE to encrypt sensitive data on the audit logs with a ranking of sensitivity. The auditor uses the audit algorithm to decide which portions of the log need to be decrypted to provide evidence of the audit decision. We use HIBE because it provides a convenient way to encrypt audit logs at a fine granularity (i.e., each event is encrypted using keys derived from the identifiers participating in that event) and limit the auditors to decrypt minimum-necessary data for audits. Since events occur frequently, but audits that require decryption of data are (presumed to be) rare, our framework provides an efficient audit procedure. We extended the audit algorithm to provide understandable explanations for accesses rather than just claiming that an access can be proved consistent with or violate the policy. We design an audit architecture that augments an HIE using the ATNA profile, a standard for auditing HIEs, and supports HIBE encryption of audit logs and an explanation-enabled audit procedure. A key feature of the design inspired by a pair of state HIEs (namely those for Maryland and Illinois) is the ability to combine the ATNA data with external documentation that is input to the audit algorithm. Our main contribution lies in the design and implementation of a practical system using this novel encryption and audit algorithm.
- Available Materials for Other Investigators/Interested parties
The CODASPY publication describes the work. Software for the prototype and the policy auditing system can be obtained by contacting the authors of publication.
- Market entry strategies
The primary market entry strategy with this work is to show how advanced techniques, particularly HIBE encryption and the Reduce algorithm can be used in conjunction with a practical audit based architecture such as the ones being considered in many state HIEs and an HIE standard for audit. For the standard we carried out the demonstration for ATNA but with an attention to the need to integrate information from sources outside of ATNA of the kind we encountered in the state of Illinois.
Bibliography
Privacy-Preserving Audit for Broker-Based Health Information Exchange
Se Eun Oh, Ji Young Chun, Limin Jia, Deepak Garg, Carl A. Gunter, Anupam Datta
ACM Conference on Data and Application Security and Privacy (CODASPY ’14), San Antonio, TX, March 2014
Building a Smarter Health and Wellness Future: Privacy and Security Challenges
Carl A. Gunter
Chapter 9 in: ICTs and the Health Sector: Towards Smarter Health and Wellness Models, OECD, pp 141-157, October 2013
Report of Preliminary Findings and Recommendations
State of Illinois Health Information Exchange Authority Data Security and Privacy Committee
September 2012
Policy Auditing over Incomplete Logs: Theory, Implementation and Applications
Deepak Garg, Limin Jia, and Anupam Datta
Proceedings of the 18th ACM CCS, 2011
