Automated Policy: HIE POLICY ENFORCEMENT
Lead Institution: Stanford
Project Leader: John C. Mitchell
Research Progress
- Abstract
Current approaches to enforcing privacy policy on medical records are usually unable to function outside of the organization where the policy originated. Suppose that a record has a policy that limits viewership to cardiologists and nurses in the cardiology ward. If the policy is shared with another organization via a health information exchange, there is no guarantee that the policy can be enforced successfully. We aim to help solve this problem by using attribute-based encryption to encode the policy cryptographically into the medical record when shared.
- Focus of the research/Market need for this project
State laws for consent require the use of information only under certain conditions with patient approval. Current EHR/EMR solutions can only enforce policies within the boundaries of their systems and do not provide adequate access control when the record leaves the originating organization.
- Project Aims/Goals
The aim of this project is to develop a way to enforce privacy policies even if a document is transmitted outside of the originating institution. To do this, we must first model the applicable policies to determine the characteristics of valid users. Once the policy has been computed, we apply attribute-based encryption (ABE) to enforce the policy at decryption time.
- Key Conclusions/Significant Findings/Milestones reached/Deliverables
Our efforts with this project have led to the following observations:
- Some access policies can be enforced on medical records without the use of a traditional server-side access control checker
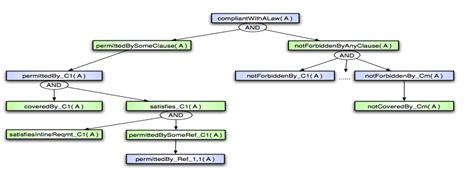
- Privacy law clauses can be encoded in first-order logic as compliance trees (Figure 1) that describe the components of the clauses.
- Changes to privacy law can be modeled and reflected in the corresponding compliance trees
- There exists a finite representative hospital database that illustrates how privacy laws may apply to different cases
- Our logic representation can be used to test and debug laws and support education
- Materials Available for Other Investigators/interested parties
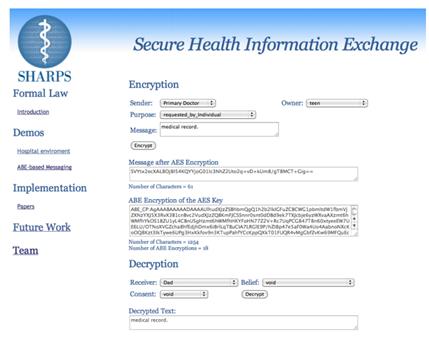
We have released a demo that generates secure messages that are encrypted with a privacy policy baked into the message itself.
- Source code: http://crypto.stanford.edu/privacy/HIPAA/IHI2012_HIE_Git.zip
- Virtual machine: http://tinyurl.com/lmcvhrq
- Market entry strategies
Current access controls used by companies such as Epic, Cerner and Intersystems cannot guarantee policy enforcement outside of the originating organization. We think that this work will benefit HIE, as it allows policy to follow the medical record as it is shared and re-shared in different contexts.
Bibliography
Declarative Privacy Policy: Finite Models and Attribute-Based Encryption
Peifung E. Lam, John C. Mitchell, Andre Scedrov, Sharada Sundaram, and Frank Wang
ACM SIGHIT International Health Informatics Symposium (IHI12), January 2012
