Audit: PERMISSION REQUEST ANALYSIS
Lead Institution: UC Berkeley
Project Leader: Dawn Song
Research Progress
- Abstract
Android and Facebook provide third-party applications with access to users’ private data and the ability to perform potentially sensitive operations (e.g., post to a user’s wall or place phone calls). As a security measure, these platforms restrict applications’ privileges with permission systems: users must approve the permissions requested by applications before the applications can make privacy- or security-relevant API calls. However, recent studies have shown that users often do not understand permission requests and are unsure of which permissions are typical for applications.
- Focus of the research/Market need for this project
App stores are an increasingly popular way to provide applications to a large number of mobile health users. Moreover, key parts of the SHARP projects focus on developing app stores. It is important to understand the security and privacy risks with these markets to aid vendors, users, and the parties that maintain the app stores to mitigate risks. Such risks may be greater in the mHealth area for apps than for average apps. This study providers a first step in developing methods for large-scale studies that may be later applied to a growing mHealth market place.
- Project Aims/Goals
-
We did a clustering analysis on a corpus of 188,389 Android applications and 27,029 Facebook applications to find patterns in permission requests. We used a method for Boolean matrix factorization to find overlapping clusters of permissions.
-
- Key Conclusions/Significant Findings/Milestones reached/Deliverables
-
We find that Facebook permission requests follow a clear structure that can be fitted well with only five patterns, whereas Android applications demonstrate more complex permission requests
-
The following figure illustrates some of measurements we made. It is a heat map for pairwise conditional probabilities for the Android permissions from the 20 most popular patterns.
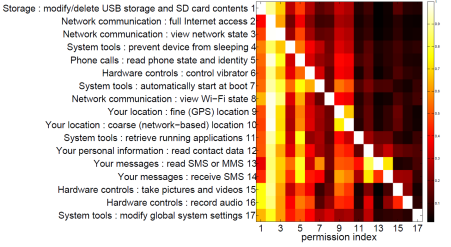
-
We also find that low-reputation applications often deviate from the permission request patterns that we identified for high-reputation applications, which suggests that permission request patterns can be indicative of user satisfaction or application quality.
-
- Materials Available for Other Investigators/interested parties
Data set at http://www.mariofrank.net/andrApps/index.html
- Market entry strategies
These techniques will be of particular interest to parties that collect and recommend groups of mHealth apps to patients and providers.
Bibliography
Mining Permission Request Patterns from Android and Facebook Applications
Mario Frank, Ben Dong, Adrienne Porter-Felt, and Dawn Song
IEEE International Conference on Data Mining, Brussels, Belgium, December 2012
Mining Permission Request Patterns from Android and Facebook Applications
Mario Frank, Ben Dong, Adrienne Porter-Felt, and Dawn Song
Extended author version arXiv:1210.2429 [cs.CR]
